Intel471
Connector Category: API Feed Source
Notice
This integration is updated to support the latest Intel471 feed ingestion endpoints. Users on Intel Exchange v3.7.6.1 and above can access the updated ingestion behavior.
Overview
What is this integration about?
Intel Exchange integrates with Intel471 to ingest up-to-date threat intelligence across multiple object types, including threat actors, malware, tools, vulnerabilities, campaigns, reports, attack patterns, indicators, observables, and locations. This integration provides rich technical details and contextual insights that help analysts better assess risks and respond to evolving cyber threats.
In Intel Exchange, the Intel471 integration retrieves the following types of threat data objects:
Threat Actor
Malware
Tool
Vulnerability
Campaign
Report
Attack Pattern
Observables
Indicators
Location
Use Cases
Utilize technical and contextual data from Adversary Intelligence and Malware Intelligence to make informed decisions and put them into action.
Gather additional details on significant vulnerabilities to assess their priority for patching.
Benefits
Get real-time and up-to-date intel feeds about emerging cyber threats, threat actors, and malicious activities.
Understand the MITRE tactics and techniques used by various threat actors.
Configure Intel471
Integrate Intel471 as a feed source and start receiving threat intel in Intel Exchange. You can use the following sections for more information:
Configure Intel471 as Feed Source
Configure Intel471 as an API feed source in Intel Exchange to receive adversary intelligence, malware intelligence, indicators, vulnerability intelligence, and finished intel report feeds from Intel471.
Before your Start
You must have the View API Feed, View Feed Source, Create Feed Source, and Update Feed Source permissions in Intel Exchange.
You must have the username and API key of your Intel471 account.
Steps
To configure Intel471 as an API feed source in Intel Exchange, follow these steps:
Go to Administration > Integration Management. In FEED SOURCES, click APIs.
Click Add API Source.
Search and select the Intel471.
Click Add Instance and enter the following details:
Instance Name: Enter a unique name to identify the instance. For example, Intel471-Prod.
Base URL: Enter the base URL of your Intel471 instance. The default base URL is
https://api.intel471.com/v1/.Username: Enter the username of your Intel471 account to authenticate communication with Intel471.
API Key: Enter the API key to authenticate with Intel471.
Verify SSL: Select this to verify the SSL certificate and secure the connection between the Intel Exchange and Intel471 servers. By default, verification is enabled.
Note
Enabling SSL verification is recommended. If you disable this option, it may result in the use of an expired SSL certificate while configuring the instance. This may not establish the connection properly, and you will not be notified in case of a broken or improper connection.
Click Save.
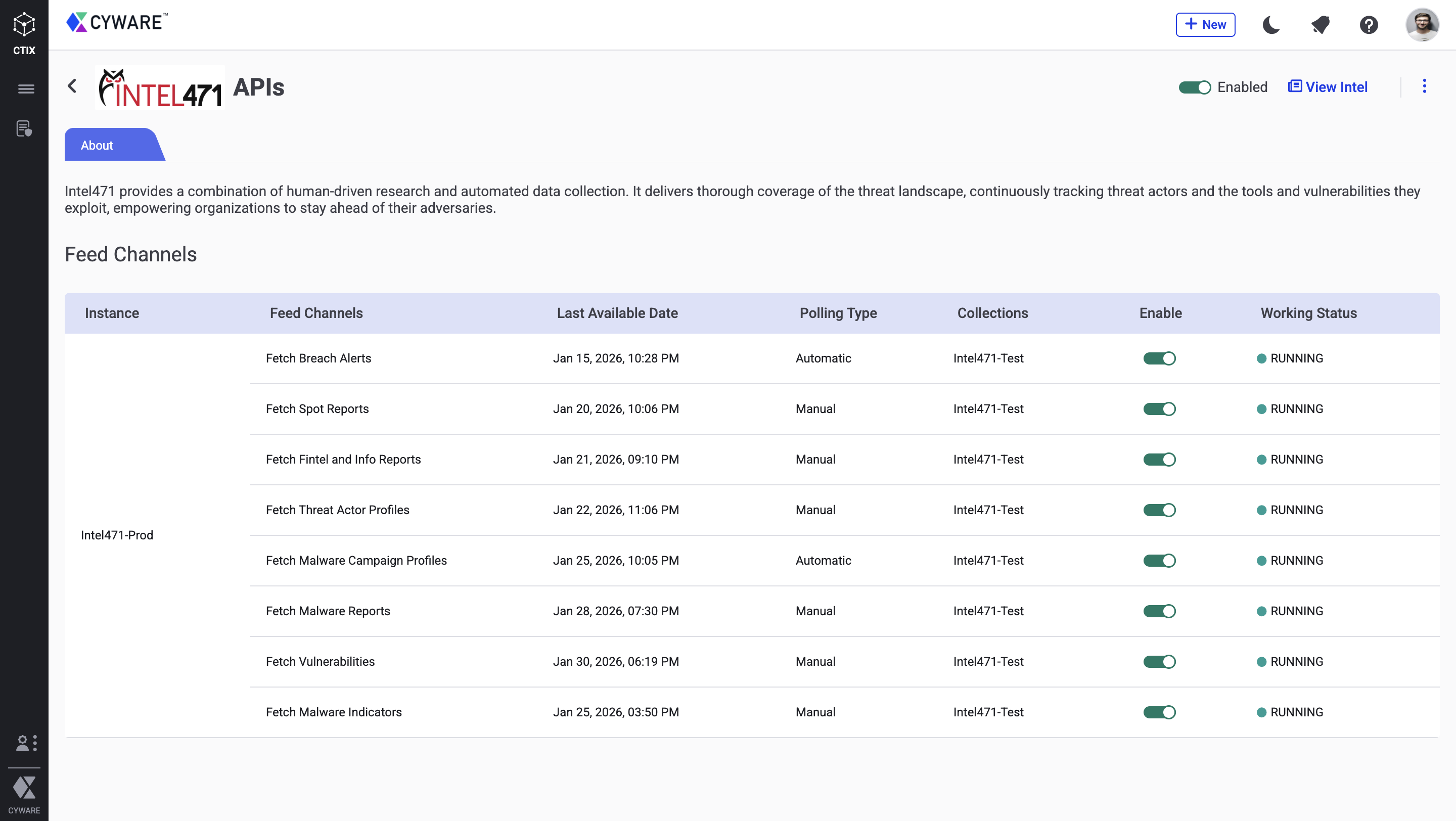
The Intel471 instance is configured, and you can view the Intel471 feed channels. You can configure multiple instances by clicking Manage > Add More.
Configure Intel471 Feed Channels
Configure the feed channels to retrieve threat data from Intel471 and store them in collections within Intel Exchange.
Steps
To configure an Intel471 channel, follow these steps:
Go to Administration > Integration Management. In FEED SOURCES, click APIs.
Search and select the Intel471.
Click the vertical ellipsis, and select Manage.
Click Manage Feed Channels.
Select a feed channel and turn on the toggle. Use the following information while configuring the channels:
Start Date and Time: Enter the date and time to start polling feeds. Select a date within 15 days from the current date.
Collection Name: Enter the name of the collection to group the feed data. For example, Intel471 Feeds. Intel Exchange creates the collection and stores all the feeds from the feed channel.
Polling Cron Schedule: Select from one of the following Polling Cron Schedule types to define when to poll the data:
Manual: Allows you to manually poll from the source collection.
Auto: Allows you to automatically poll for threat intel from sources at specific time intervals. The default polling cron schedule is Auto. Enter a frequency in minutes between 240 and 10080 minutes in Polling Time. The default polling time is 1440 minutes.
TLP: Set the TLP for the feeds that do not have a TLP already assigned. The default TLP is Amber. Alternatively, you can select None to ensure that no TLP is assigned to the feeds.
Default Source Confidence: Enter the confidence score for the feeds that do not have a confidence score already assigned. The default confidence score is 100.
Deprecates after: Specify the number of days after which the threat data (indicator) will be marked as deprecated, unless the source defines its own expiry duration. The allowed range is 1-180 days.
Custom Score: Select the Relevance and Severity Score for the channel.
Default Tags: Select any tags to identify and categorize the feeds.
Click Save.
The following sections describe additional configuration fields for specific Intel471 feed channels.
Fetch Vulnerabilities
Includes the following additional fields:
Vulnerability Status: Select the vulnerability status values to filter intel while fetching vulnerability data. All values are selected by default and can be modified as required.
Risk Level: Select the risk levels to filter vulnerabilities during ingestion. All values are selected by default and can be modified as required.
Fetch Malware Indicators
Includes the following additional field:
Filter IOCs by Intel471 Confidence Level(s): Select one or more confidence levels to filter incoming malware indicators. By default, Intel Exchange selects Medium and High to help you focus on actionable intelligence. Select additional values only if you need broader visibility.
The feed channel is configured, and you can poll feeds from the channel. You can enable the other feed channels, poll feeds, and view the feeds.
Test Feed Channel Connectivity
Test the connectivity of the Intel471 feed channels to ensure that the connection with the correct API endpoint is established and that you have permission to poll feeds.
Before you Start
Ensure that the Intel471 feed source is enabled.
Ensure that the feed channel for which you want to test connectivity is enabled.
Steps
To test the connectivity of a feed channel, follow these steps:
Go to Administration > Integration Management. In FEED SOURCES, click APIs.
Search and select the Intel471.
On a feed channel, click the vertical ellipsis and select View Details.
In the Working Status section, click Test Connectivity.
If the connection is established, then the working status shows Running. If the connectivity is broken, then the working status shows a Connection Error. Hover over the tooltip next to Connection Error to view the error code.
Note
When a feed channel loses connectivity, it is automatically disabled, and the system attempts to restore connectivity three times per hour. If the connectivity is successfully restored, the feed channel is automatically re-enabled.
To understand the error code and troubleshoot broken connectivity, see Troubleshoot Integrations.
Intel471 Feed Channels
The following table lists the feed channel and the API endpoint used to retrieve feeds from Intel471:
Feed Channel | API Endpoint |
|---|---|
Fetch Breach Alerts |
|
Fetch Spot Reports |
|
Fetch Fintel and Info Reports |
|
Fetch Threat Actor Profiles |
|
Fetch Malware Campaign Profiles |
|
Fetch Malware Reports |
|
Fetch Vulnerabilities |
|
Fetch Malware Indicators |
|
Changelog
The following table lists the changelog for each version of this integration:
Version | Release Date | Changes |
|---|---|---|
v3.7.6.1 | 06 February, 2026 | Updates Intel471 feed ingestion endpoints to align with current ingestion behavior. |