- General Documents
- Use Cases
- Cyware Products
- Use the ATT&CK Navigator with Cyware Products
Use the ATT&CK Navigator with Cyware Products
Category: Cyware Product
Cyware Products Used:
Cyware Threat Intelligence eXchange (CTIX)
Cyware Fusion and Threat Response (CFTR)
Orchestrate (CO)
Problem Statement
Security teams are always on the lookout for ways to predict, prevent and respond to cyber threats. This has led to an increase in the demand and consumption of threat intelligence. However, without a reliable framework in place, security teams find it difficult to apply threat intelligence to analyze and identify the threats targeting their organization.
Solution
To prevent this, security teams can leverage indicators of compromise (IOCs) collected through disparate sources to predict threat attackers’ behavior by mapping their tactics, techniques, and procedures (TTPs). This is where the MITRE ATT&CK framework comes into the picture.
What is MITRE’s ATT&CK framework?
MITRE’s ATT&CK framework describes how adversaries penetrate and move laterally across networks by escalating privileges, and evading your defenses. The ATT&CK framework organizes adversary behaviors into a series of tactics and techniques from the perspective of the adversaries. Examples of tactics include Defense Evasion, Lateral Movement, and Exfiltration. Within each tactic, the framework includes a series of techniques. Each technique describes one way in which the adversary tries to achieve the objective.
Understand how Adversaries Operate
Using the knowledge provided by MITRE ATT&CK framework, you can learn how threat actors execute their attacks and plan to detect and respond to threats.
The MITRE ATT&CK framework also maintains a library of information about selected threat actors and the campaigns they have conducted. This allows security teams to correlate specific adversaries with the techniques they use in their attacks.
The MITRE ATT&CK framework helps organizations identify the techniques adversaries are likely to use. This helps security teams to evaluate the defenses and strengthen them where they matter most.
Use ATT&CK Navigator with CSAP
The MITRE ATT&CK Navigator framework is built within the CSAP platform to help analysts break down the attack lifecycle and analyze each phase of a cyber attack from the received alerts and threat intel.
Analysts can map tactics and techniques to provide contextualized insights into the TTPs leveraged by threat actors while publishing alerts and intel. The below screenshot shows a sample alert mapped with relevant tactics and techniques for sharing with members of the organization.
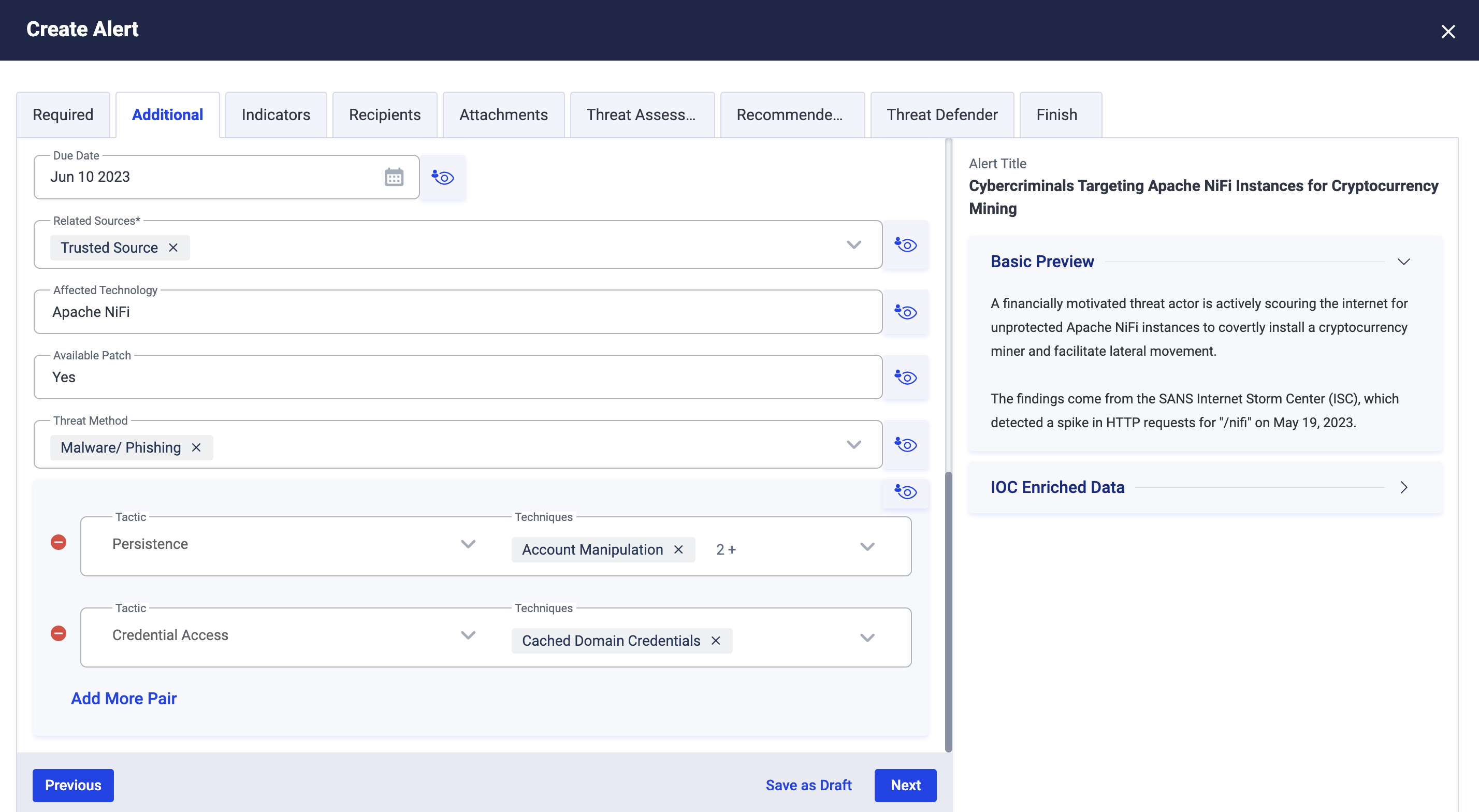
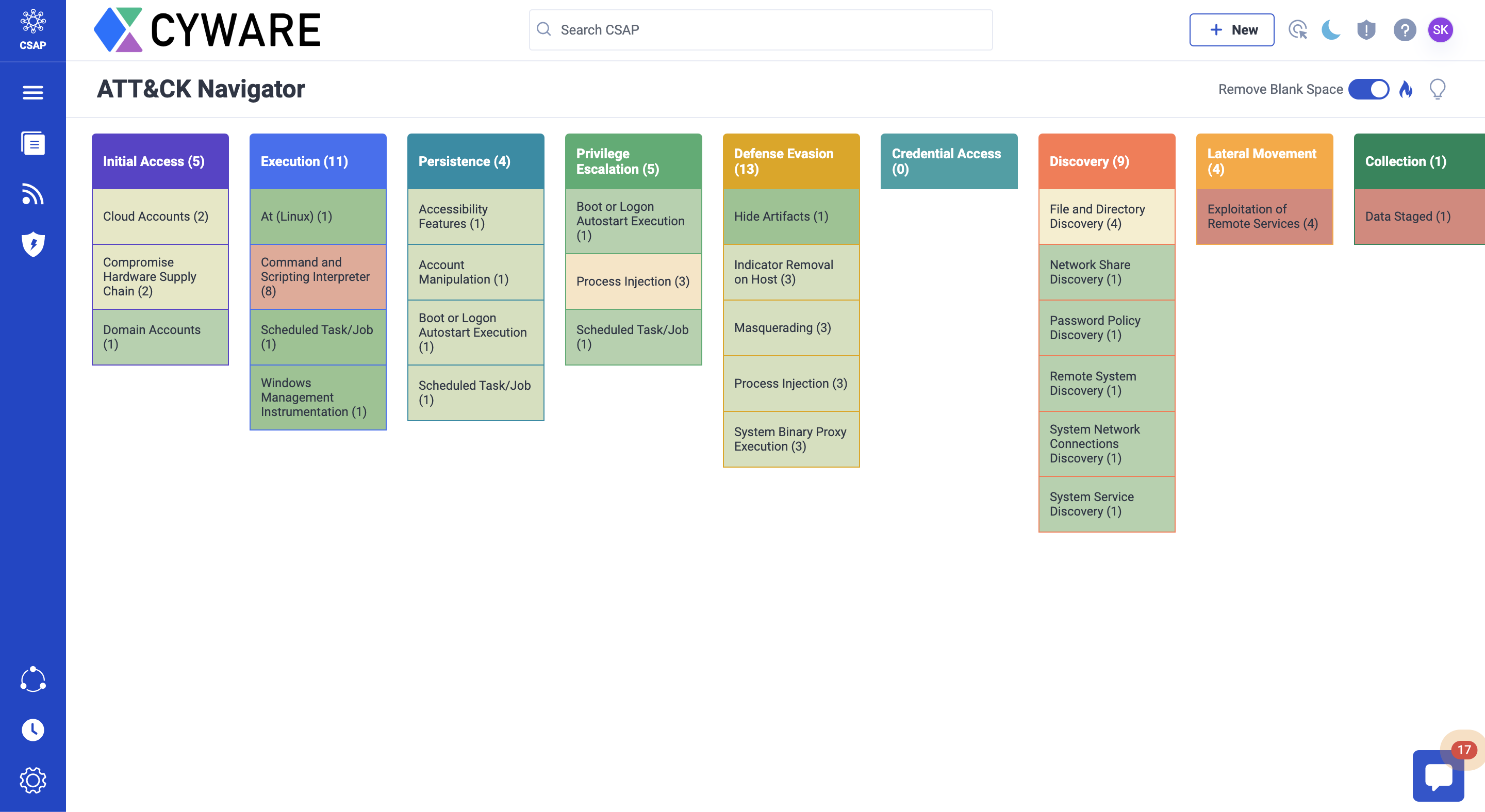
CSAP users can view adversary tactics and techniques, as a heat map, to devise threat models and defensive strategies for your organization. Different types of cyber tactics are displayed in columnar format, as well as the number of times the tactic or technique is spotted in alerts and intel.
Use ATT&CK Navigator with CTIX
CTIX integrates with the MITRE ATT&CK framework, along with support for sub-techniques and matrices for different ATT&CK environments such as Enterprise and Mobile. CTIX analysts benefit greatly from the clear classification of threats that enables analysts to better assess the coverage of an attack technique with their existing defenses and provides quick insights of the most critical threats facing your organization. Different types of cyber tactics are displayed in columnar format, as well as the number of times the tactic or technique is spotted in indicators and threat actors.
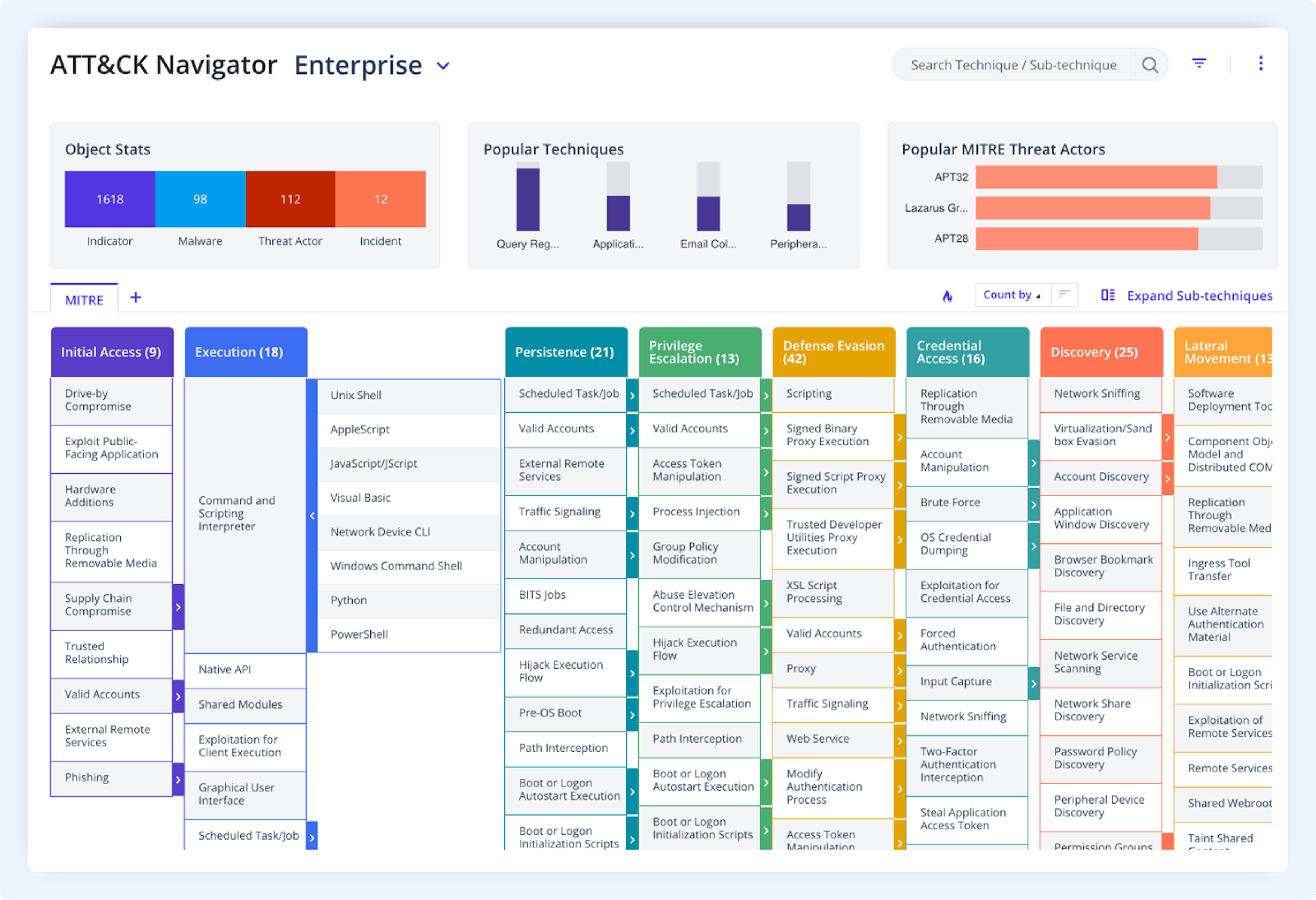
The MITRE ATT&CK Navigator empowers organizations to deduce contextual threat intelligence and take quick decisions to defend against threats. It provides a common standardized framework that is globally accessible, allowing threat intel teams to work together with data to compare, detect and respond to threats.
Security analysts and defenders can create and share threat intelligence related to the behavior of attackers. Collaboratively, they can create and share threat-based knowledge by closing the information gaps that attackers attempt to exploit.
The ATT&CK Navigator provides a roadmap for security teams to apply in their operational controls and realize their weaknesses and strengths against certain threat actors.
To know more about CTIX ATT&CK Navigator, see .
Use ATT&CK Navigator with CFTR
CFTR integrates with the MITRE ATT&CK framework to act as a reference for incident response teams who can learn the nature of threats they encounter and methods to alleviate those threats. By using ATT&CK as a reference for new threats, they can plan ahead and assess their overall cybersecurity strategy and bridge the gaps they discover. Different types of cyber tactics are displayed in columnar format, as well as the number of times the tactic or technique is spotted in incidents, malware, indicators, and threat actors.
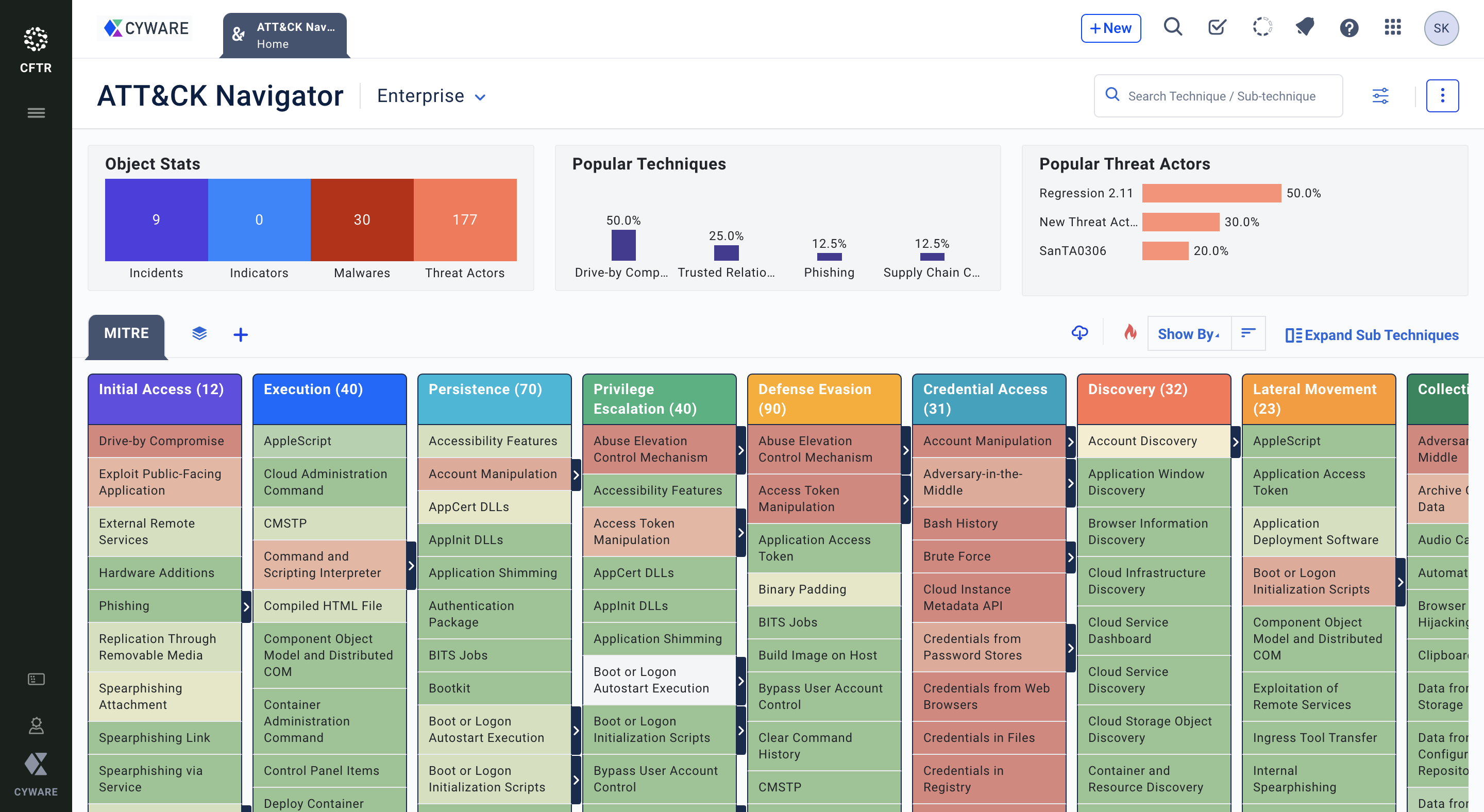
The MITRE ATT&CK framework can be used at different phases of the threat response lifecycle.
Detection and Analysis: SOCs and incident response teams can leverage ATT&CK techniques and tactics to assess defensive strengths, weaknesses, and operational issues. They validate controls, detect or uncover known and unknown threats, and identify misconfigurations.
Containment: The containment stage is when security teams take steps to contain the threat. ATT&CK empowers them with updated malicious signatures, IOC identification, contextual analysis of SIEM logs, providing tactical insights on moving abused hosts to a controlled environment for further monitoring, and much more.
Eradication and Recovery: Security teams assess attacks for ATT&CK framework compliance, rectify any identified misconfigurations, update signatures, utilize SIEM for correlation analysis, and leverage the internal workflow to promptly address alerts.
Learnings: This process is often provided less significance, but it is important. ATT&CK Navigator can help security teams summarize the incident and see if the countermeasures will work in the long run.
To know more about CTIX ATT&CK Navigator, see .
Common Functionalities offered by ATT&CK framework for CTIX and CFTR users
The ATT&CK Navigator gives a quick overview of the object statuses, popular techniques observed, and the popular MITRE-listed threat actors detected.
Using the ATT&CK matrix, for each technique, analysts can view the affected platforms, data sources, associated malware, the defenses it can bypass, and the required mitigation and detection methods.
The ATT&CK Navigator also shows the indicators, malware, threat actors, or incidents related to the technique, along with examples and further references. By visiting the Relations tab, analysts can use the Threat Visualizer to view the IOCs associated with a specific ATT&CK technique more effectively.
Analysts can switch between Enterprise and Mobile ATT&CK matrix to view different sets of techniques that affect corresponding assets, and switch to the MITRE ATT&CK Heatmap view for a color-coded representation of critical MITRE tactics and techniques.
Analysts can also search for specific top-level techniques or sub-techniques associated with particular platforms, threat actors, software, and log data sources.
Analysts can add custom layers with their chosen techniques, sub-techniques. Custom layers are for users to visualize organized information related to the MITRE ATT&CK Framework. MITRE ATT&CK Navigator tool layers offer customizable views of the navigator, so users can focus on specific aspects of the framework. Here are some ways the MITRE ATT&CK Navigator tool can use layers:
Tactic and techniques layers
Threat actor layers
Importing layers
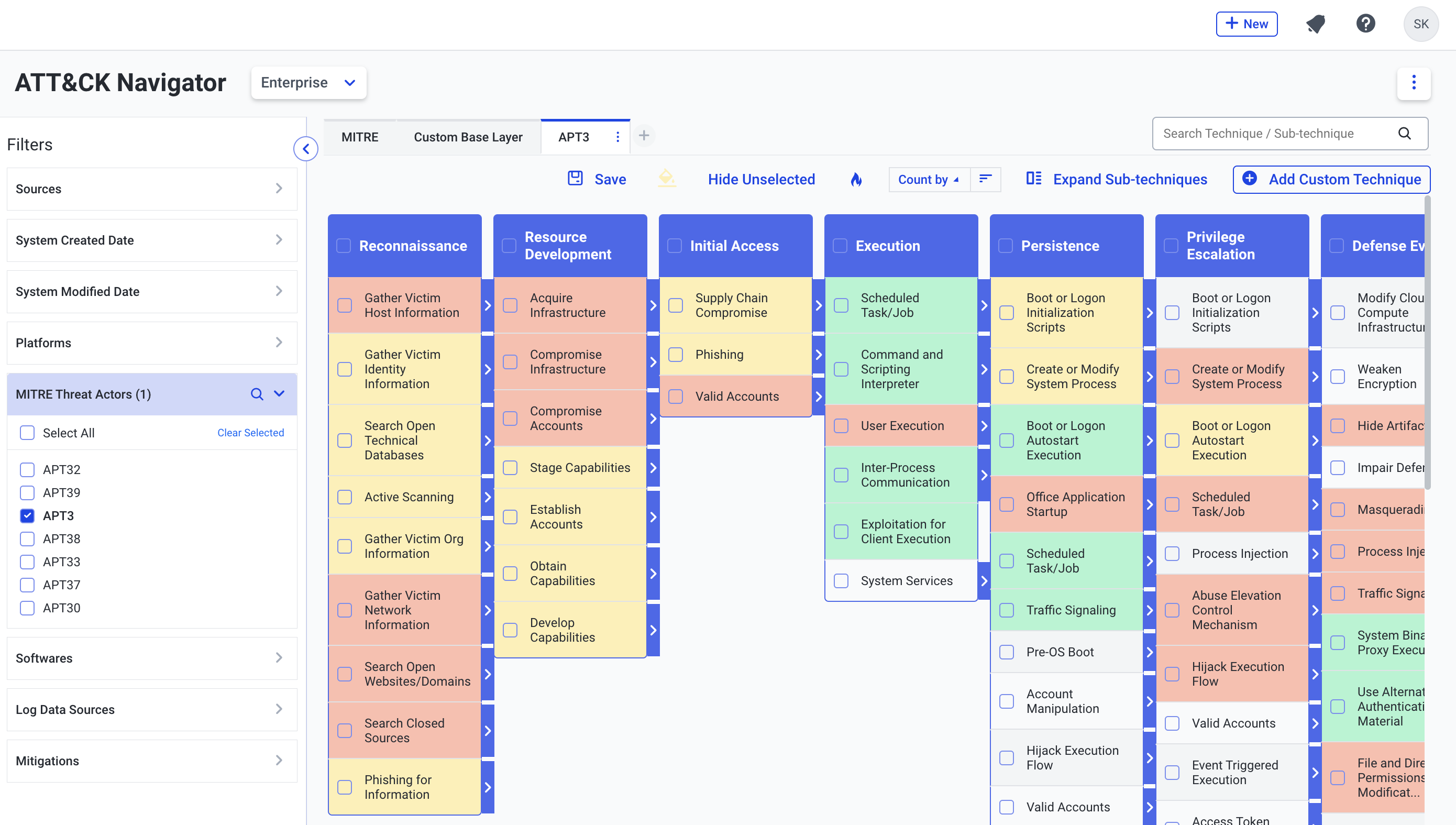
Custom Layers
The below screenshots show a sample custom layer for the APT3 threat actor group with color codes configured. The colors denote scores as (1 - RED) (2 - YELLOW) (3 - GREEN). While 1 denotes a low score, 3 denotes a high score for a technique.
Benefits
Improved SOC Operations
The ATT&CK framework enables the security teams to connect and know the flow of an attack, and identify the security gaps and faults, thus enabling them to prioritize their response activities. SOC teams can also use the ATT&CK Framework to evaluate their defensive measures, detected techniques, red and blue team planning, threat intelligence analysis, and comprehensive incident response process.
Heat Map Creation
The ATT&CK framework is useful in creating heat maps of frequently used adversarial tactics, techniques, and procedures. This allows security teams to audit and analyze systems, tools, controls, and policies for any malicious behavior.
Reduced MTTD and MTTR
Security teams can calibrate their detection operations to the most prevalent intrusion scenarios and related tactics and techniques available in the MITRE ATT&CK framework. This saves analysts time in detecting incidents. Using the framework, security teams can also deploy the required course of action to protect the systems and assets.